As the men who dare to Rob Olympics headlines, Song 喆 encountered interception. This Carnival sex is not only for all the entertainment, science and technology circle of God into it:If there is no participation of the majority of hacking enthusiasts, paparazzi seem powerless within days pulled out the Song 喆 life, hobbies, address, room records, described pieces without too much.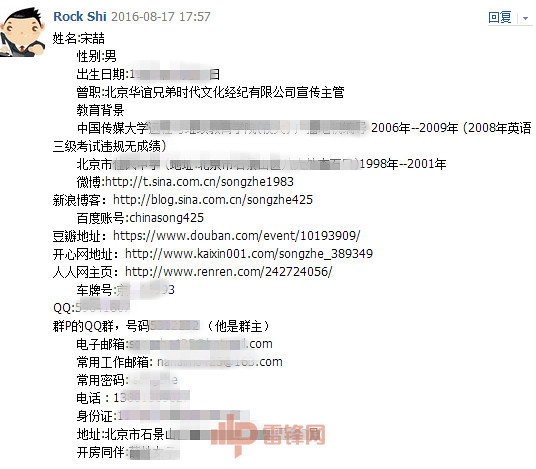
 "Friends Song 喆 personal information summary (protect citizen privacy, sensitive information have been coding)"In fact, hackers caught rape seriously, you can get many surprise singular information bar that fell. Lei feng's network decided to ask top hackers, legal and moral considerations aside for the time being, how human a person? Or conversely, if you accidentally fell in love with the star's wife and became a public enemy, and how to avoid the misery of human flesh?This network of Lei feng has interviewed curvy entertainment qualities and spirit of professional hackers security boss Wei Lin–360, a researcher at the network attack and defense laboratories. Following are dry. Incipio iPhone 6+ caseA time bomb, iPhone–carry-onTalk to suppress, take out your iPhone. (If you have one)Open: set-privacy-registration services-system services-frequented locationsSee no, let me guess, you go to is where most of your home, and second, is the company for you. If it is not detailed enough, and point into a map. Is such a horror. https://www.youtube.com/watch?v=FNEE7fSBlEQ
"Friends Song 喆 personal information summary (protect citizen privacy, sensitive information have been coding)"In fact, hackers caught rape seriously, you can get many surprise singular information bar that fell. Lei feng's network decided to ask top hackers, legal and moral considerations aside for the time being, how human a person? Or conversely, if you accidentally fell in love with the star's wife and became a public enemy, and how to avoid the misery of human flesh?This network of Lei feng has interviewed curvy entertainment qualities and spirit of professional hackers security boss Wei Lin–360, a researcher at the network attack and defense laboratories. Following are dry. Incipio iPhone 6+ caseA time bomb, iPhone–carry-onTalk to suppress, take out your iPhone. (If you have one)Open: set-privacy-registration services-system services-frequented locationsSee no, let me guess, you go to is where most of your home, and second, is the company for you. If it is not detailed enough, and point into a map. Is such a horror. https://www.youtube.com/watch?v=FNEE7fSBlEQ 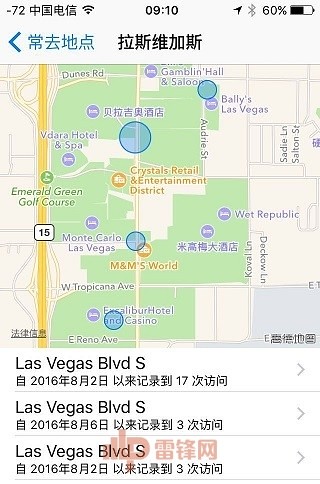 "IPhone open by default" go "function, complete record of your life"If hackers get your iCloud account with any iPhone landing, can have access to your location information. So if you're the enemy, don't be surprised if God horse the next day someone on your block in your way downstairs.Of course, it was not so complicated, see the "find my iPhone" yet?However all the information are established on the basis of your iCloud break. ICloud security depend to a large extent, to the strength of your passwords and secret security mailbox password strength. If your secret security mailbox is NetEase, hehe.
"IPhone open by default" go "function, complete record of your life"If hackers get your iCloud account with any iPhone landing, can have access to your location information. So if you're the enemy, don't be surprised if God horse the next day someone on your block in your way downstairs.Of course, it was not so complicated, see the "find my iPhone" yet?However all the information are established on the basis of your iCloud break. ICloud security depend to a large extent, to the strength of your passwords and secret security mailbox password strength. If your secret security mailbox is NetEase, hehe.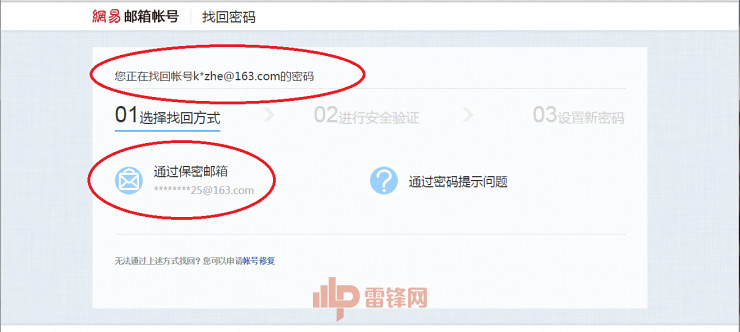 "Song 喆 mailbox used to retrieve your secret security mailbox using the same weak passwords, this leads to a hacker can easily modify his email password"It's not funny, Song 喆 common mailbox is NetEase, which is why he breached one of the key points. Judging from the Internet Ma Rong self-timer, these sources are likely to be Ma Rong, or Song 喆 iPhone mobile phones. This most likely means that hacker conquered two people have at least one mobile phone.Second, weak passwords-papered door locksReal-world case, Song 喆 all mailboxes within a few days, and renren, Jingdong account seems to have been breached. How hackers do it? According to the burst of information, Lin Wei-we simply Combs his "social worker" step:1, mobile phone number, ID card information was leaked by users through social workers. (ID card contains the address, but later proved to homes have been sold. )2, NetEase email password cracking involved behind the secret security and other frequently used mailboxes.3, use watercress account mail everyone NET, was done.4, the mailboxes passwords are the same, or similar, Jing dong, popular reviews, takeout App was broken up.5, a business delivery address exposed, leading to hide addresses were pulled out, was surrounded by the media.We granted that everything started from a mailbox be cracked. It is well known that NetEase mailbox users many, used weak passwords of users, are likely to be targeted attacks by hackers breached. Because of this, can see Song 喆 mailbox password in the social work library.About science. Now almost all user information website has been "salted", that is, all the user names and passwords are stored in encrypted state. Even if hackers into the Web server, and get your password information, nor read the clear text, but need a password dictionary to decipher. Decipher is directly proportional to the difficulty and the complexity of the password. This means that if your password is complex enough to present computer is still difficult to break.In fact, the seemingly clever Song 喆 network security awareness is not an ordinary person, his password is simply appalling. Rather, his password is your First Name, or add their own birthday. This led to a series of accounts within a short time break the tragic plight of.So the question comes, how to set a password secure?William Lim told Lei Feng network, password should be the same as movies, divided into at least three levels:First level:ICloud micro QQ password, passwords, PayPal password, you should set up more than ten, meaningless characters alphanumeric symbols in vertical (if you appreciate semantic memory password, you can use a skill, that is to use 0 instead of o, replace I with 1, and so on. )Second level:Jing dong, purchase, take-out and other commonly used Web sites, sets more than eight, meaningless characters alphanumeric symbols in vertical. Note password arranged not with first-level passwords have some overlap, otherwise once a secondary password is cracked, can directly to secondary password as a dictionary, easy to crack the level code.Third level:General Web site, in order to take care of herself IQ can be used relatively weak easy to remember password. Also note passwords cannot be and other levels have repeatedly or easily fall short.
"Song 喆 mailbox used to retrieve your secret security mailbox using the same weak passwords, this leads to a hacker can easily modify his email password"It's not funny, Song 喆 common mailbox is NetEase, which is why he breached one of the key points. Judging from the Internet Ma Rong self-timer, these sources are likely to be Ma Rong, or Song 喆 iPhone mobile phones. This most likely means that hacker conquered two people have at least one mobile phone.Second, weak passwords-papered door locksReal-world case, Song 喆 all mailboxes within a few days, and renren, Jingdong account seems to have been breached. How hackers do it? According to the burst of information, Lin Wei-we simply Combs his "social worker" step:1, mobile phone number, ID card information was leaked by users through social workers. (ID card contains the address, but later proved to homes have been sold. )2, NetEase email password cracking involved behind the secret security and other frequently used mailboxes.3, use watercress account mail everyone NET, was done.4, the mailboxes passwords are the same, or similar, Jing dong, popular reviews, takeout App was broken up.5, a business delivery address exposed, leading to hide addresses were pulled out, was surrounded by the media.We granted that everything started from a mailbox be cracked. It is well known that NetEase mailbox users many, used weak passwords of users, are likely to be targeted attacks by hackers breached. Because of this, can see Song 喆 mailbox password in the social work library.About science. Now almost all user information website has been "salted", that is, all the user names and passwords are stored in encrypted state. Even if hackers into the Web server, and get your password information, nor read the clear text, but need a password dictionary to decipher. Decipher is directly proportional to the difficulty and the complexity of the password. This means that if your password is complex enough to present computer is still difficult to break.In fact, the seemingly clever Song 喆 network security awareness is not an ordinary person, his password is simply appalling. Rather, his password is your First Name, or add their own birthday. This led to a series of accounts within a short time break the tragic plight of.So the question comes, how to set a password secure?William Lim told Lei Feng network, password should be the same as movies, divided into at least three levels:First level:ICloud micro QQ password, passwords, PayPal password, you should set up more than ten, meaningless characters alphanumeric symbols in vertical (if you appreciate semantic memory password, you can use a skill, that is to use 0 instead of o, replace I with 1, and so on. )Second level:Jing dong, purchase, take-out and other commonly used Web sites, sets more than eight, meaningless characters alphanumeric symbols in vertical. Note password arranged not with first-level passwords have some overlap, otherwise once a secondary password is cracked, can directly to secondary password as a dictionary, easy to crack the level code.Third level:General Web site, in order to take care of herself IQ can be used relatively weak easy to remember password. Also note passwords cannot be and other levels have repeatedly or easily fall short. "Provide a strong password for children's shoes reference, don't blame me when you forget"Three, micro-circle of friends-the latent + infernalDo you know all of your app friends? I believe you will answer "no". So, how do you determine your circle of friends is lurking in an infernal?If you see the app has not seen for years old classmates and friends, watch avatar actually met, you will pass the validation, please? Normal in all likelihood will pass validation.But the truth may be: hackers all you and buddy information publicly on the Internet, get your old school photos and basic information, and then hid behind the app to add you as a friend.Once adopted, your circle of friends will open to hackers. Think about it, you bask in every photo in a circle of friends, a feeling that it can become a hacker to determine your location and character of the evidence.William Lim says:Most people in your circle of friends when you send content, without a high level of vigilance. If strangers to add you as a friend, and seems more credibility when you'd he shielded his circle of friends, and then add friends and view each other's circle of friends, once trusted each other's identity has been established, and then he let go of your circle of friends.Four, microblogging, renren, watercress-good-bye, privacySong 喆 emptied after the incident, the first thing his Twitter, he also realized that the information they posted on Twitter, is going to be to their detriment "in a Court of law." However, he is not the first time emptying his renren. (Most people really hard to realize that there are people who network the first time the existence of this artifact. ) This led to the hacker stole into his mailbox, change the password for a network of others who. It is likely that he has been unable to access their network for all accounts.
"Provide a strong password for children's shoes reference, don't blame me when you forget"Three, micro-circle of friends-the latent + infernalDo you know all of your app friends? I believe you will answer "no". So, how do you determine your circle of friends is lurking in an infernal?If you see the app has not seen for years old classmates and friends, watch avatar actually met, you will pass the validation, please? Normal in all likelihood will pass validation.But the truth may be: hackers all you and buddy information publicly on the Internet, get your old school photos and basic information, and then hid behind the app to add you as a friend.Once adopted, your circle of friends will open to hackers. Think about it, you bask in every photo in a circle of friends, a feeling that it can become a hacker to determine your location and character of the evidence.William Lim says:Most people in your circle of friends when you send content, without a high level of vigilance. If strangers to add you as a friend, and seems more credibility when you'd he shielded his circle of friends, and then add friends and view each other's circle of friends, once trusted each other's identity has been established, and then he let go of your circle of friends.Four, microblogging, renren, watercress-good-bye, privacySong 喆 emptied after the incident, the first thing his Twitter, he also realized that the information they posted on Twitter, is going to be to their detriment "in a Court of law." However, he is not the first time emptying his renren. (Most people really hard to realize that there are people who network the first time the existence of this artifact. ) This led to the hacker stole into his mailbox, change the password for a network of others who. It is likely that he has been unable to access their network for all accounts.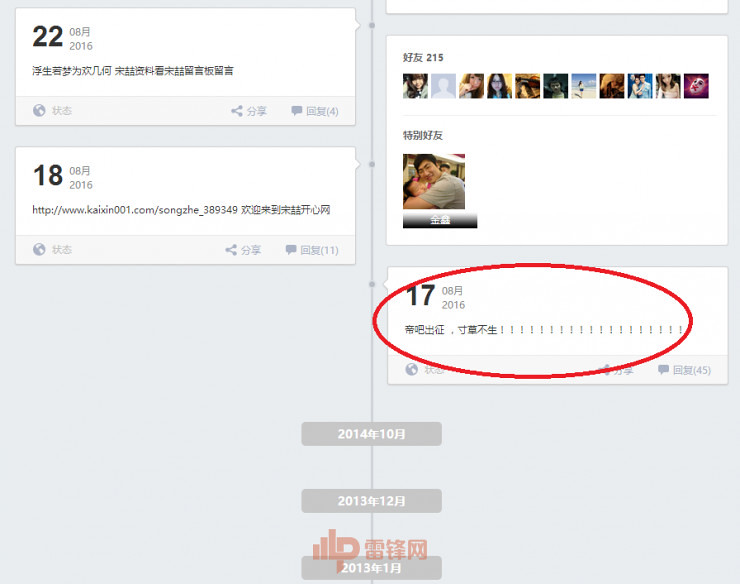 "Look, the Emperor's friends have taken the Song 喆 renren"You may ask, Song 喆 why not everyone through email network password change back? The answer is that his e-mail was exposed following the already has a flood of Internet users all over the world try to logon into abnormal protection status, no one has been able to land on. In addition, even if there is no such human DDoS, mentioned earlier, his mailbox was key may have been compromised and modified, so Song 喆 has lost its control over your mailbox.Think about what you are all done online? The social platform, already had a little gas, you lurk in all black history. A case study of Song 喆, everyone on-line, you can open a query to his birthday, from small to large school information, he likes dogs, his idol is Edison Chen, his Bohemian personality, and so on.Will be referred to later, when crack other account or mailbox, such personal information as secret security question answers, crack played an important role.
"Look, the Emperor's friends have taken the Song 喆 renren"You may ask, Song 喆 why not everyone through email network password change back? The answer is that his e-mail was exposed following the already has a flood of Internet users all over the world try to logon into abnormal protection status, no one has been able to land on. In addition, even if there is no such human DDoS, mentioned earlier, his mailbox was key may have been compromised and modified, so Song 喆 has lost its control over your mailbox.Think about what you are all done online? The social platform, already had a little gas, you lurk in all black history. A case study of Song 喆, everyone on-line, you can open a query to his birthday, from small to large school information, he likes dogs, his idol is Edison Chen, his Bohemian personality, and so on.Will be referred to later, when crack other account or mailbox, such personal information as secret security question answers, crack played an important role. "Dan Tan in the Twitter friends two pictures leading to home position"Again talk about Twitter, assuming that being meat did not empty the first time, everyone can view he published the information publicly. Because Tweets are the things of the flesh, have become almost routine:Wang Dan has since released a picture taken from the window, by netizens based on residential interiors, window height, illumination, navigate within a few hours of her community, the floor number and number.Liu and female assistants also released photos of the same bowl of tomato, which is suspected of cheating by users underground.
"Dan Tan in the Twitter friends two pictures leading to home position"Again talk about Twitter, assuming that being meat did not empty the first time, everyone can view he published the information publicly. Because Tweets are the things of the flesh, have become almost routine:Wang Dan has since released a picture taken from the window, by netizens based on residential interiors, window height, illumination, navigate within a few hours of her community, the floor number and number.Liu and female assistants also released photos of the same bowl of tomato, which is suspected of cheating by users underground. "Song 喆 to his reputation as a bulldog open microblogging" tabby small DD a happy life ", user photos to navigate his community of life"As one possess top security awareness white hat hackers, Wei Lin also Twitter, renren to express emotion, but he posted some tips for Twitter:Try not to shoot photos that contain too much information, also try not with location information. Try not to use the argot of some people can understand, because if someone is stalking you when code can easily be cracked.Five-, trumpet-holding-the hidden clues a secretWhen people do bad things, usually with a small.
"Song 喆 to his reputation as a bulldog open microblogging" tabby small DD a happy life ", user photos to navigate his community of life"As one possess top security awareness white hat hackers, Wei Lin also Twitter, renren to express emotion, but he posted some tips for Twitter:Try not to shoot photos that contain too much information, also try not with location information. Try not to use the argot of some people can understand, because if someone is stalking you when code can easily be cracked.Five-, trumpet-holding-the hidden clues a secretWhen people do bad things, usually with a small.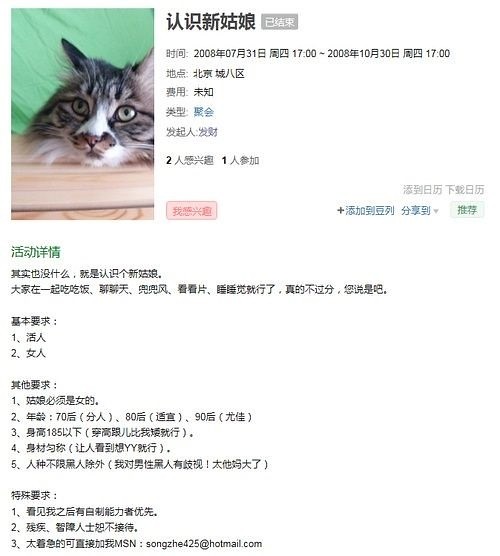 "About the girl, the Song 喆 's post, revealed that NetEase mailbox is not a common, but a Hotmail mailbox"Song 喆 also understands this, so in the watercress around "group p" when leaving is not a common mailbox. But in fact, watercress landed his mailbox and the relationship between the small mailbox has been linked.When registering a lot of small, people will choose to use a separate mailbox, but a lot of people tend not to buy a new phone to receive the verification code, even if there are two mobile phone numbers of people, would still use a living or work. This will establish a virtual link between the ID and the real ID.Some people have small QQ, but in order to facilitate the management, are often mutually add friend, even base. In this case, once the QQ password has been compromised, it is easy to take out your trumpet QQ. If the size, use the same password, you can easily be afternoon.Lin Wei said.In fact, according to the Insider leaks, Song 喆 common and small mailboxes using a similar weak passwords, which led to a hacker directly into the Song 喆 small mailbox, see his dark side.
"About the girl, the Song 喆 's post, revealed that NetEase mailbox is not a common, but a Hotmail mailbox"Song 喆 also understands this, so in the watercress around "group p" when leaving is not a common mailbox. But in fact, watercress landed his mailbox and the relationship between the small mailbox has been linked.When registering a lot of small, people will choose to use a separate mailbox, but a lot of people tend not to buy a new phone to receive the verification code, even if there are two mobile phone numbers of people, would still use a living or work. This will establish a virtual link between the ID and the real ID.Some people have small QQ, but in order to facilitate the management, are often mutually add friend, even base. In this case, once the QQ password has been compromised, it is easy to take out your trumpet QQ. If the size, use the same password, you can easily be afternoon.Lin Wei said.In fact, according to the Insider leaks, Song 喆 common and small mailboxes using a similar weak passwords, which led to a hacker directly into the Song 喆 small mailbox, see his dark side.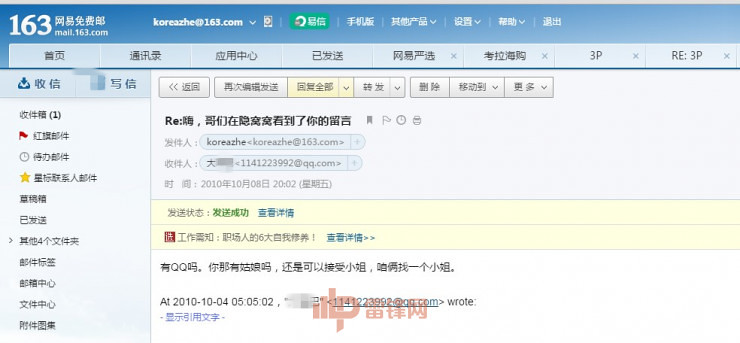 "Song 喆 a small mailbox is an anonymous hacker attack, the network provides a screenshot of Lei feng, forbidden under the age of 18 years old"However, for trumpet and identity correlation, much more than that simple, Wei Lin cited a number of facts:If you use the same device landed on King micro and small micro-letters, then at the micro data level, for those two numbers must be associated.If you are anonymous to use Baidu search some keywords, there are ads pop up in your device. These are the forced Association in the service provider's data.In this light, small specification for highest security level probably is as follows:Anonymous 1, apply for a phone card2, in a special application on the platform of a temporary dynamic mailbox3, to the temporary mailbox mailbox as a key, applying for new permanent mailbox4, using a new private phone logs on trumpet, and not on any other device landed on the trumpet5, two cell phones and cannot at the same time with me, in case the location information overlap, associate; open Wi-Fi is strictly prohibited to prevent fishing location.Believe me, if the Song 喆 trumpet about guns for this security level, there are few people around the world can be found.Of course, this "senior trumpet Guide" is just a joke. Wei Lin summarizes: If you want to use small to protect their privacy, virtual identity and the real identity of the cut as possible.Six, take-away, Jingdong, Taobao–sell your shipping addressPublic Song 喆 "encirclement" and ultimately human flesh into the reality of human flesh on the network. Finally according to various information media have successfully intercepted the Song 喆, essential in this crime, is likely to be.Wei Lin believes that Taobao for user information in these giant enterprises, micro-letter protection level is very high, there was no leak. However, if the password rating mentioned earlier of not doing it, hit the library will occur (hackers cracked the password of other platforms, which use these passwords to land on Taobao and the app).Such public comments, hungry, Jingdong these platforms, and the security level may be weaker than BAT "biological" platform.In short, information leaks, would have a fatal impact, that is your shipping address. These delivery address authenticity is very high, and are likely to include "human flesh" and relatives of all commonly used addresses.
"Song 喆 a small mailbox is an anonymous hacker attack, the network provides a screenshot of Lei feng, forbidden under the age of 18 years old"However, for trumpet and identity correlation, much more than that simple, Wei Lin cited a number of facts:If you use the same device landed on King micro and small micro-letters, then at the micro data level, for those two numbers must be associated.If you are anonymous to use Baidu search some keywords, there are ads pop up in your device. These are the forced Association in the service provider's data.In this light, small specification for highest security level probably is as follows:Anonymous 1, apply for a phone card2, in a special application on the platform of a temporary dynamic mailbox3, to the temporary mailbox mailbox as a key, applying for new permanent mailbox4, using a new private phone logs on trumpet, and not on any other device landed on the trumpet5, two cell phones and cannot at the same time with me, in case the location information overlap, associate; open Wi-Fi is strictly prohibited to prevent fishing location.Believe me, if the Song 喆 trumpet about guns for this security level, there are few people around the world can be found.Of course, this "senior trumpet Guide" is just a joke. Wei Lin summarizes: If you want to use small to protect their privacy, virtual identity and the real identity of the cut as possible.Six, take-away, Jingdong, Taobao–sell your shipping addressPublic Song 喆 "encirclement" and ultimately human flesh into the reality of human flesh on the network. Finally according to various information media have successfully intercepted the Song 喆, essential in this crime, is likely to be.Wei Lin believes that Taobao for user information in these giant enterprises, micro-letter protection level is very high, there was no leak. However, if the password rating mentioned earlier of not doing it, hit the library will occur (hackers cracked the password of other platforms, which use these passwords to land on Taobao and the app).Such public comments, hungry, Jingdong these platforms, and the security level may be weaker than BAT "biological" platform.In short, information leaks, would have a fatal impact, that is your shipping address. These delivery address authenticity is very high, and are likely to include "human flesh" and relatives of all commonly used addresses.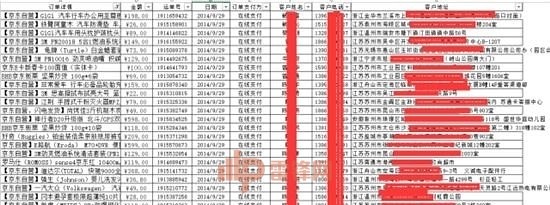 "Black circulating in the Middle East order disclosure of information"Entertainment reporters have not been named, but William Lim concluded that final "informant" navigate to the Song 喆 "hideout" (actually his parents purchased a new home), probably as a result of a business delivery address leakage. In addition, if Song 喆 sell software (for example, hungry of America) master password has been hackers once he ordered takeout in their hiding places, your meal will address immediately to betray him. Incipio iPhone 6 CaseFrom e-commerce and the leaking of information delivery platform, and more. For example, hackers broke, Song 喆 Jingdong shopping records, there are plenty of dog food, so he may sooner or later, you're walking the dog.Seven, the Wi-Fi–eye of GodYou might not believe that, as long as your phone turned on Wi-Fi, hackers could in theory a way, track your space movement.Let popular science:All phones open Wi-Fi, foreign broadcasts in real time once names connected to Wi-Fi, and as long as the Wi-Fi signal within the same name, phone will automatically try to connect.This is a miracle of a Wei Lin are difficult to understand.William Lim envisages such an attack pattern:First Song 喆 doorstep, with a casual search Wi-Fi signal, the signal is the strongest Song 喆 Wi-Fi under the Wi-Fi,Mark name in the home.Then use what is known as "Diablo" Wi-Fi transmitter, outgoing and Song 喆jia Wi-Fi signal with the same name.Finally the "Diablo" in the song zhe has likely places, once a mobile phone connected to the Wi-Fi signal, the "big pineapple" will return to the control signal.
"Black circulating in the Middle East order disclosure of information"Entertainment reporters have not been named, but William Lim concluded that final "informant" navigate to the Song 喆 "hideout" (actually his parents purchased a new home), probably as a result of a business delivery address leakage. In addition, if Song 喆 sell software (for example, hungry of America) master password has been hackers once he ordered takeout in their hiding places, your meal will address immediately to betray him. Incipio iPhone 6 CaseFrom e-commerce and the leaking of information delivery platform, and more. For example, hackers broke, Song 喆 Jingdong shopping records, there are plenty of dog food, so he may sooner or later, you're walking the dog.Seven, the Wi-Fi–eye of GodYou might not believe that, as long as your phone turned on Wi-Fi, hackers could in theory a way, track your space movement.Let popular science:All phones open Wi-Fi, foreign broadcasts in real time once names connected to Wi-Fi, and as long as the Wi-Fi signal within the same name, phone will automatically try to connect.This is a miracle of a Wei Lin are difficult to understand.William Lim envisages such an attack pattern:First Song 喆 doorstep, with a casual search Wi-Fi signal, the signal is the strongest Song 喆 Wi-Fi under the Wi-Fi,Mark name in the home.Then use what is known as "Diablo" Wi-Fi transmitter, outgoing and Song 喆jia Wi-Fi signal with the same name.Finally the "Diablo" in the song zhe has likely places, once a mobile phone connected to the Wi-Fi signal, the "big pineapple" will return to the control signal. "Diablo wireless signal transmitter (Pineapple Wireless)"This kind of "Diablo" can have many (if you have enough funds for adultery), arrangement in the residential garage door, the corridor door, all he may stay. In this way, just like in the cities covered with cameras, as long as the received signal, show trackers (or family friend) over here. (Can be done by connecting the device name to determine the specific identity of the connection. )"Diablo" can not only provide false Wi-Fi signal, can also provide Wi-Fi capability. However, these "fishing Wi-Fi" is transmitted clear text information can be exploited at a glance.Due to the miracle of attack is based on Wi-Fi protocols, so Wei Lin also said there is no good defense. "Turn on Wi-Fi only when necessary, is a helpless way. ”What wonderful workAbove many in Beijing city "pursuit" method. However, experienced human and social workers "public enemies" is likely the first time flying abroad. How to judge whether a person "escaping" out?"Did you hear about air travel vertically and horizontally? "William Lim asked.
"Diablo wireless signal transmitter (Pineapple Wireless)"This kind of "Diablo" can have many (if you have enough funds for adultery), arrangement in the residential garage door, the corridor door, all he may stay. In this way, just like in the cities covered with cameras, as long as the received signal, show trackers (or family friend) over here. (Can be done by connecting the device name to determine the specific identity of the connection. )"Diablo" can not only provide false Wi-Fi signal, can also provide Wi-Fi capability. However, these "fishing Wi-Fi" is transmitted clear text information can be exploited at a glance.Due to the miracle of attack is based on Wi-Fi protocols, so Wei Lin also said there is no good defense. "Turn on Wi-Fi only when necessary, is a helpless way. ”What wonderful workAbove many in Beijing city "pursuit" method. However, experienced human and social workers "public enemies" is likely the first time flying abroad. How to judge whether a person "escaping" out?"Did you hear about air travel vertically and horizontally? "William Lim asked.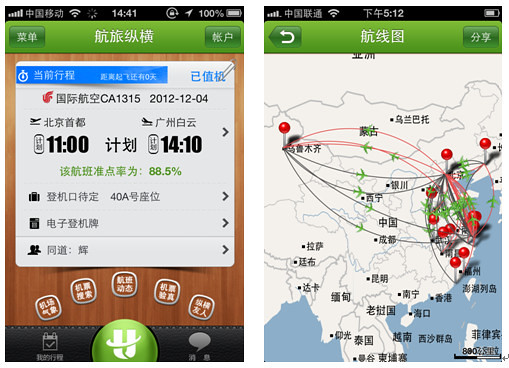 "Air travel vertically and horizontally"Children's shoes in many frequent fliers are using air travel vertically and horizontally, it can render all of one complete flight information. In the last version, you just enter your ID number, you can check your flight. Also, you enter another person's identification number, you can also view other people's voyage.William Lim told Lei feng's network (search for "Lei feng's network", public interest), in the new version of air travel in vertical and horizontal, App to query the identity verification become more stringent, requiring users to upload their own ID photos.He said:In that case, an attacker is more trouble. PS you need an ID card.Yes, audit staff is difficult to distinguish between the authenticity of an ID card."Another Flash card also has the function of a wonderful feature. "William Lim added," If you use NFC devices to read it, will be spending the last decade. This attack is only need to scan it with the device at the other side as well, containment when the Song 喆 those of entertainment reporters, not just interviews, should also use this device to scan him. ”
"Air travel vertically and horizontally"Children's shoes in many frequent fliers are using air travel vertically and horizontally, it can render all of one complete flight information. In the last version, you just enter your ID number, you can check your flight. Also, you enter another person's identification number, you can also view other people's voyage.William Lim told Lei feng's network (search for "Lei feng's network", public interest), in the new version of air travel in vertical and horizontal, App to query the identity verification become more stringent, requiring users to upload their own ID photos.He said:In that case, an attacker is more trouble. PS you need an ID card.Yes, audit staff is difficult to distinguish between the authenticity of an ID card."Another Flash card also has the function of a wonderful feature. "William Lim added," If you use NFC devices to read it, will be spending the last decade. This attack is only need to scan it with the device at the other side as well, containment when the Song 喆 those of entertainment reporters, not just interviews, should also use this device to scan him. ”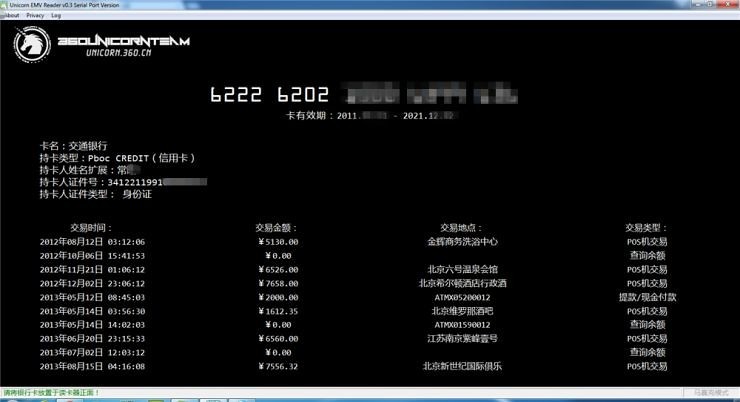 "Use specific NFC devices to scan the card, card number, card holder name and ID number, and the last ten transactions can be read/picture provided by the 360 Team Unicorn"William Lim said as a hacker, pay attention to gongxinweishang. If only in order to find the Song 喆, then the above tips to spare. However, people wanted was the truth. And get to the truth of premise, it is Song 喆 and Ma Rong two cracks.Lin Wei, Song 喆 room records circulated on the network, it is ' a. Objectively speaking, detailed hour open records, only the police can master. So the source of this information never seems to have any answers, the police are certainly not clarified. This result is, never be able to prove the authenticity of the recording. Further, assume that this record is a hacker forged, so to a certain extent had a record of adding to the mutual suspicion of the two results.
"Use specific NFC devices to scan the card, card number, card holder name and ID number, and the last ten transactions can be read/picture provided by the 360 Team Unicorn"William Lim said as a hacker, pay attention to gongxinweishang. If only in order to find the Song 喆, then the above tips to spare. However, people wanted was the truth. And get to the truth of premise, it is Song 喆 and Ma Rong two cracks.Lin Wei, Song 喆 room records circulated on the network, it is ' a. Objectively speaking, detailed hour open records, only the police can master. So the source of this information never seems to have any answers, the police are certainly not clarified. This result is, never be able to prove the authenticity of the recording. Further, assume that this record is a hacker forged, so to a certain extent had a record of adding to the mutual suspicion of the two results.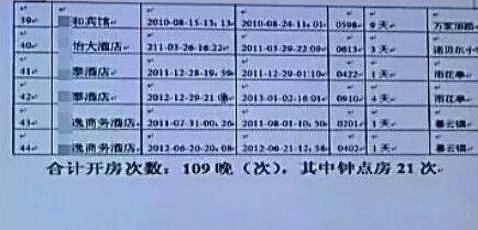 "Net exposure Song 喆 room records"Suddenly woke up. The highest realm of hackers, is in the human spirit planted a time bomb in the world.Time to spread positive energy. As a senior hacker, William Lim knows that legal and ethical boundaries.Social workers access to others ' accounts were illegal acts, suicide is unethical behavior of others. These attacks, is because in the age of the Internet, everyone is facing the threat of attacks. Known attack methods can be more effective defense.He said.From this point on, Song 喆 's tragic history teaches us at least two reasons:
"Net exposure Song 喆 room records"Suddenly woke up. The highest realm of hackers, is in the human spirit planted a time bomb in the world.Time to spread positive energy. As a senior hacker, William Lim knows that legal and ethical boundaries.Social workers access to others ' accounts were illegal acts, suicide is unethical behavior of others. These attacks, is because in the age of the Internet, everyone is facing the threat of attacks. Known attack methods can be more effective defense.He said.From this point on, Song 喆 's tragic history teaches us at least two reasons: Take care of your wife, don't touch someone else's wife;Take care of your passwords, don't touch other people's passwords.
Take care of your wife, don't touch someone else's wife;Take care of your passwords, don't touch other people's passwords.